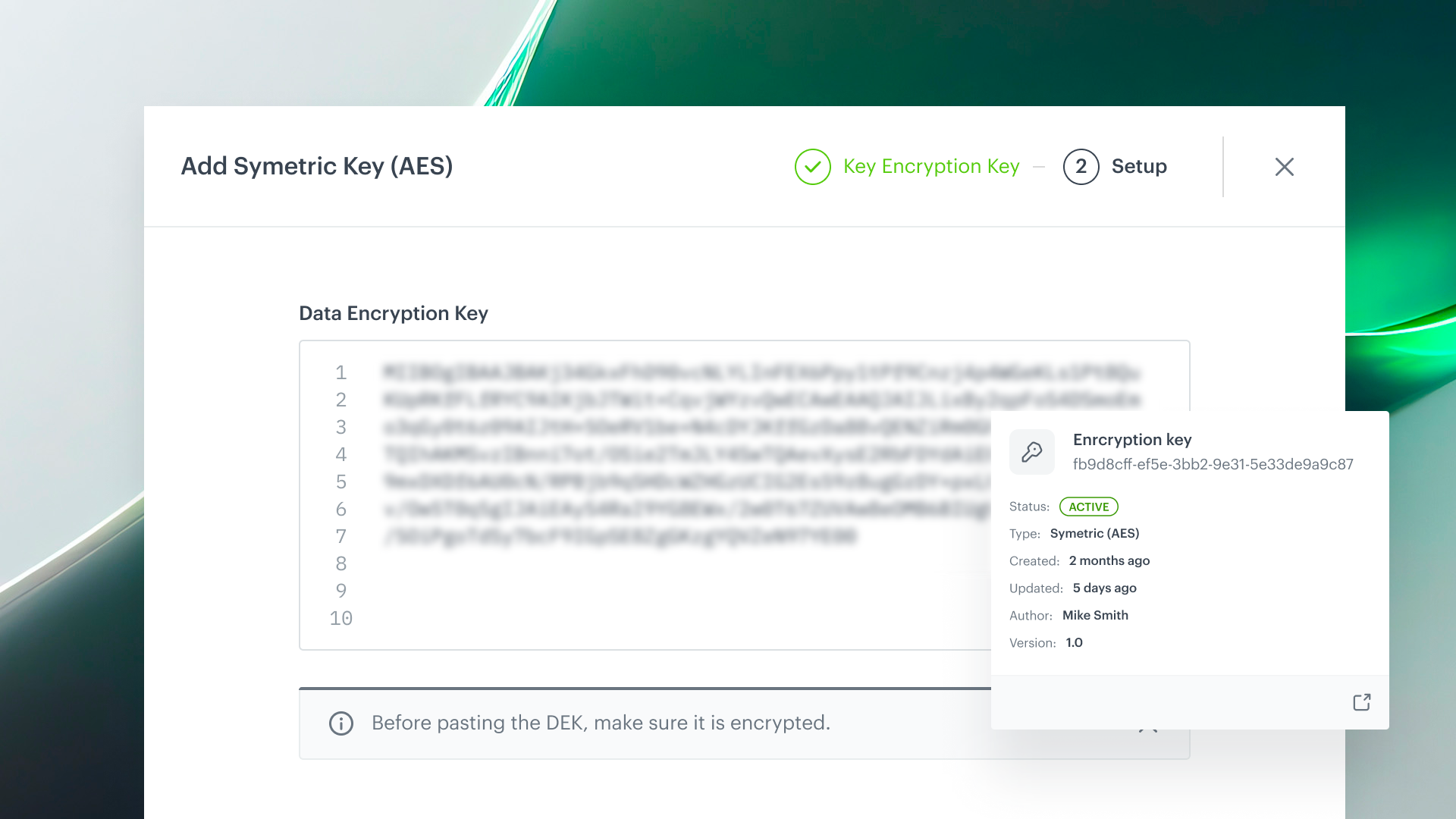
At Synerise, we prioritize data security and control at every level. In alignment with the advanced security needs, our Automation module provides integrated, application-level encryption for even greater user control. This feature provides the necessary tools to secure data at every step of the workflow, designed to help businesses meet the highest standards of data protection without adding complexity to their operations.
✅ Stronger protection for sensitive data - use industry-standard AES-256 encryption to protect your data during transfers.
✅ Support for compliance and security policies - whether you’re following GDPR, internal governance rules, or industry regulations, these tools help you align with strict data handling requirements.
✅ Full ownership of encryption - with BYOK, maintain full ownership and control over your encryption keys, manage their versions, lifecycle, and status.
✅ Easy to apply, no technical expertise required - encryption can be enabled through clear settings and step-by-step controls — no need for custom code or IT involvement.
✅ Confidence in every connection - from first integration to daily operation, your data is protected using the same encryption standards trusted by governments and global enterprises.

At Synerise, we prioritize data security and control at every level. In alignment with the advanced security needs, our Automation module provides integrated, application-level encryption for even greater user control. This feature provides the necessary tools to secure data at every step of the workflow, designed to help businesses meet the highest standards of data protection without adding complexity to their operations.
✅ Stronger protection for sensitive data - use industry-standard AES-256 encryption to protect your data during transfers.
✅ Support for compliance and security policies - whether you’re following GDPR, internal governance rules, or industry regulations, these tools help you align with strict data handling requirements.
✅ Full ownership of encryption - with BYOK, maintain full ownership and control over your encryption keys, manage their versions, lifecycle, and status.
✅ Easy to apply, no technical expertise required - encryption can be enabled through clear settings and step-by-step controls — no need for custom code or IT involvement.
✅ Confidence in every connection - from first integration to daily operation, your data is protected using the same encryption standards trusted by governments and global enterprises.